CIS Benchmark In Behavox: Part 2 - Docker

Hi, I'm Cesar Augusto Sanchez, a Senior SRE at Behavox. Some time ago, we explained how we achieved CIS benchmark compliance for Linux OS.
Today, I will describe our approach to securing our containerized systems in compliance with the CIS Benchmark guidelines for Docker.
Goals and overview
In today's cloud-native landscape, Docker has become an essential tool for containerization. However, its widespread adoption creates a critical need for security. The CIS Docker Benchmark provides comprehensive guidelines to secure Docker containers.
In this post, I'll walk you through an application I developed to automate the validation of Docker instances against these benchmarks using the docker-bench GO tool.
Why Secure Docker?
Securing Docker environments is crucial for several reasons:
- Isolation: Containers share the host OS kernel and, in some cases, filesystem - making them less isolated than virtual machines.
- Vulnerabilities: Misconfigurations and vulnerabilities can expose containers to security risks, including breaking out of container isolation.
- Compliance: Many industries have compliance requirements that mandate secure configurations.
Solution
The solution comprises a GO daemon that executes the docker-bench tool, analyzes the results, and reports metrics. This approach ensures continuous monitoring and real-time reporting of Docker security compliance.
Architecture
- Docker Hosts: Machines running Docker to be scanned.
- Docker Bench application: Aquasecurity docker-bench go application
- CIS Docker Scanner Application: Behavox cis-docker-scanner go application
- Invokes the docker-bench tool on docker hosts
- Processes docker-bench JSON output for test results
- Generates metrics
- Vmagent: metrics scrapper
- Grafana: to visualize results
How It Works
cis-docker-scannerservice starts and initializes the metricscis-docker-scannerexecutes the docker-bench tool on specified hostscis-docker-scannercaptures JSON output containing test results and parses its output to categorize tests as pass, fail, warn, info or skippedcis-docker-scannergenerates metrics based on test outcomesvmagentcollects metrics and sends them to Behavox's central observability service- Grafana dashboards are updated, and alerts are generated if needed
Benefits
- Automation: Eliminates the need for manual compliance checks.
- Continuous Monitoring: Provides real-time visibility into Docker security status.
- Scalability: This can be easily deployed across multiple Docker hosts.
Grafana Dashboard
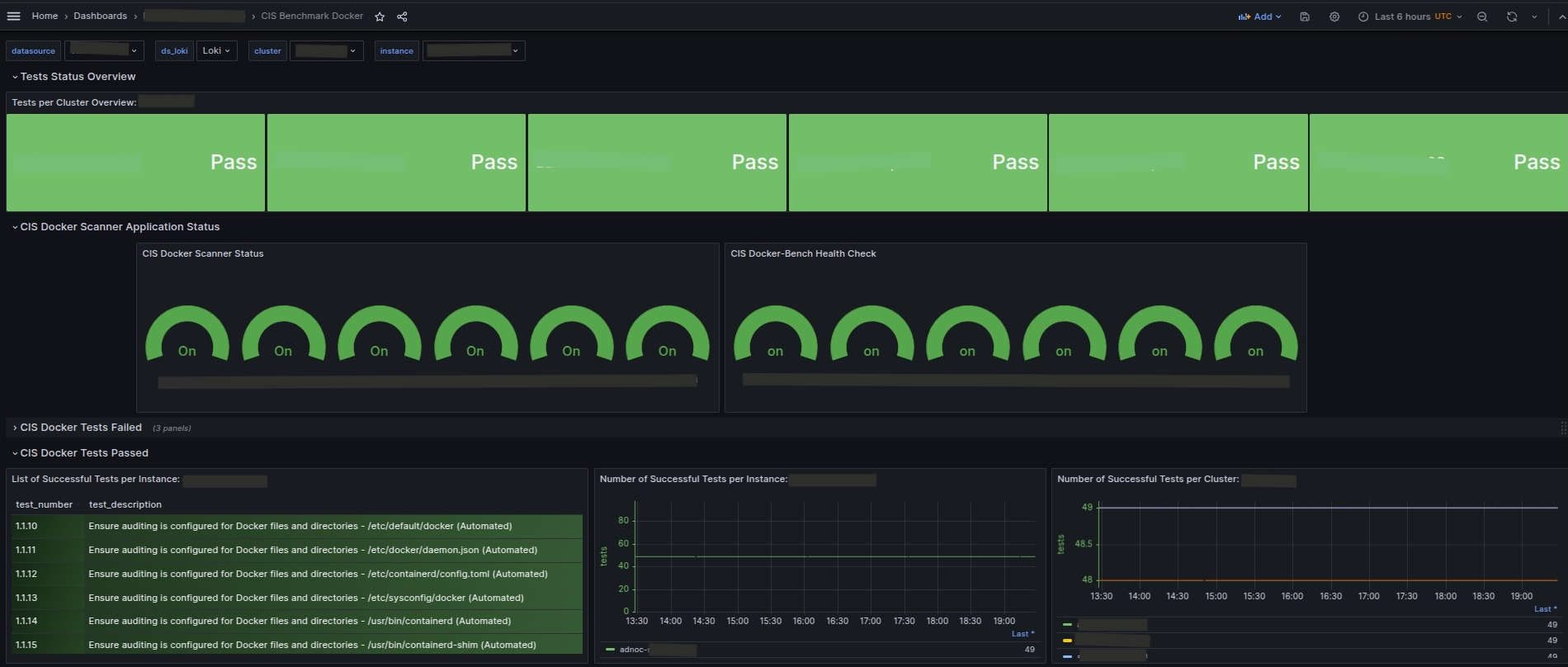
The dashboard presents panels with information and visualization that show the tests in different states: failed, success, warning, informational, and ignored.
In addition to our dashboard, we configured our monitoring system to fire an alert depending on the criticality of the related issue, so that our on-call team could react as soon as possible to a potential problem.
Conclusion
Automating the security validation of Docker environments using an in-house tolling and the docker-bench tool is a robust approach to ensuring continuous compliance with CIS benchmarks. This solution automates the scanning process and provides real-time metrics for proactive security management.
By adopting this automated approach, our organization significantly enhanced the security posture of our Docker environments and ensured they remained compliant with industry standards.
🛠️ Behavox is looking for talented engineers to join us in building the world’s leading AI-powered Archiving, Compliance and Security solutions. If you're interested, check out our careers page.
